Network attacks refer to attacks on the hardware, software and data in the network system by exploiting the vulnerabilities and security flaws in the network, mainly including malicious software, phishing, etc. Ransomware is one of the malware that is used to encrypt files and folders, thereby preventing access to important files, and usually requires a ransom in exchange for decryption keys. If you do not pay the ransom, you can only give up all the precious data previously stored in the computer, but even after the ransom is paid, the redemption of the data is still not guaranteed.
A few weeks ago, Colonial Pipeline Co., the largest gasoline pipeline operator in the United States just became a target of ransomware. It is reported that JBS, the world's largest meat producer, has also been attacked recently, causing some servers failed to work properly. With the rapid development of network attack technologies and attack tools, most companies and home and small office users who do not have advanced defense systems are now facing information security issues and real-time threats from ransomware.
1. Regularly update applications and operating systems
Strengthen computer security. Facts have proved that outdated computer systems are relatively easier to be the target of ransomware.
2. Install critically acclaimed security tools
Installing the safe antivirus software or mainstream security tools can help detect and combat malicious threats and provide additional protection.
3. Autonomously identify suspicious files
Be vigilant at all times, and do not open email attachments or click on files from unknown sources before making sure they are safe. Pay attention to identifying files with suspicious hidden names, such as PDF files with ".pdf.exe" protected by EXE passwords.
4. Disable the remote access
Malware often regards the use of Remote Desktop Protocol (RDP) as the main target. Disabling RDP when remote access is not required can effectively block attacks from malicious software.In the face of increasingly powerful and changeable network attacks and malicious software, antivirus software may not be able to detect their existence in time. Once attacked, you will face huge losses. Even if the ransom is paid, there is no guarantee that the data will be returned! Therefore, it is strongly recommended that you make regular backups of all data in order to restore the infected files and minimize the damage. TerraMaster NAS solution can help you.
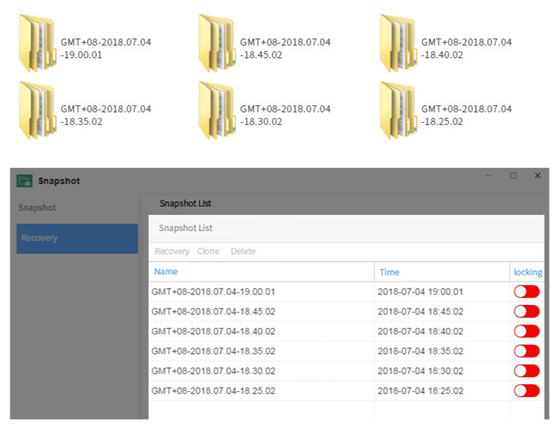
1. More advanced file system
Both EXT 4 and Btrfs file systems are supported at the same time. The Btrfs file system introduces advanced storage technology and Snapshot technology to prevent data damage and reduce maintenance costs. While improving the high degree of data integrity, it can also provide flexible and efficient data protection and recovery tools.
2. Extensive backup options
A variety of backup tools (AOMEI Backupper, Time Machine, Duple Backup, Centralized Backup, USB Copy, Cloud Sync), which can realize PC backup to TNAS, server backup to TNAS, virtual machine backup to TNAS, TNAS backup to TNAS, TNAS backup to Cloud disk, cloud disk backup to TNAS, USB backup to TNAS, TNAS backup to USB, meet almost all data backup requirements, and support multi-version backup, incremental backup, scheduled backup, and one-key restore.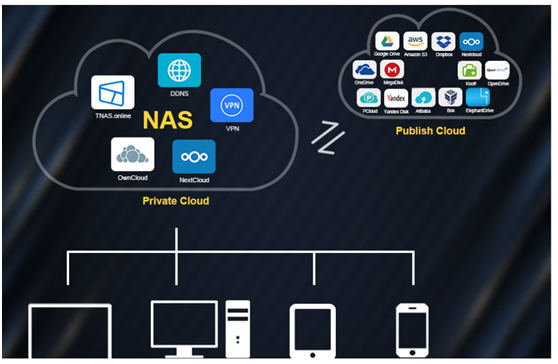
3. Support synchronization of multiple cloud drives
The device supports data synchronisation with a variety of popular cloud drives, including Google Drive, Amazon S3, Dropbox, OneDrive, pCloud, Yandex Disk, Alibaba Cloud OSS, Box, ElephantDrive, Koofr, MegaDisk, Nextcloud, and OpenDrive. The user simply selects the appropriate synchronisation directory and policy.
4. Multi-layer security protection
Data is often an invaluable asset for enterprises or individuals, and malicious attacks on the network will expose your data to huge risks. TNAS not only supports SSL encryption, firewall, DoS anti-malicious attack, account protection, but also has a special advanced security mode to keep your device at the highest level of security.
If you encounter a ransomware attack unfortunately, after detecting the infection, you can isolate the ransomware process and prevent its further spread. If it is in a cloud environment, just mining and isolating the source of the ransomware attack can help contain the infection, thereby reducing the damage to the data. After confirming that the computer has no risk of infection, restore all data through the backup function of the TerraMaster NAS device.


